Teleport
Open-source platform that provides unified, audited, identity-based access to servers, Kubernetes clusters, databases, and desktops without static credentials.
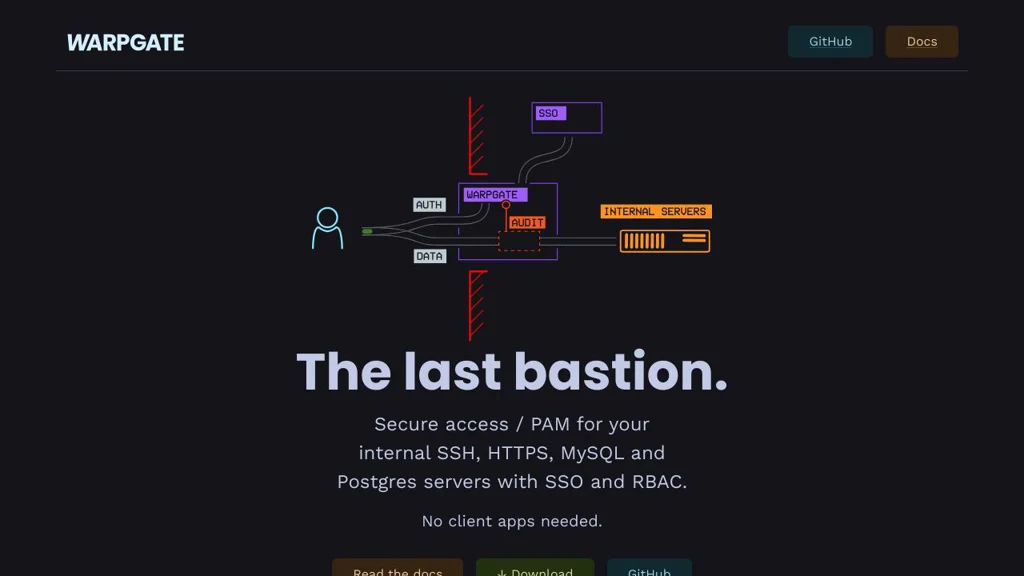
Teleport is an identity-native access platform that unifies secure access to infrastructure (SSH), Kubernetes, databases, web apps, and desktops through a single control plane. It focuses on eliminating long-lived credentials by using short-lived certificates and strong identity, while providing centralized visibility and audit trails.
Key Features
- Unified access proxy for SSH, Kubernetes, databases, Windows desktops (RDP), and internal web apps
- Short-lived, automatically issued certificates (no shared SSH keys) and session-based access
- Built-in audit logging and session recording/playback (SSH and Kubernetes activity; RDP recording in supported editions)
- Role-based access control (RBAC) with fine-grained policies and access workflows
- Single sign-on integrations (e.g., SAML/OIDC providers) and device-aware access options
- Infrastructure discovery and inventory (nodes, clusters, apps, databases) with a central web UI and CLI (
tsh) - High availability and clustering for running Teleport at scale
Use Cases
- Replace bastion hosts and shared SSH keys with centralized, identity-based SSH access
- Provide secure, auditable Kubernetes access for platform and developer teams
- Centralize database access with consistent authentication, authorization, and auditing
Limitations and Considerations
- Some capabilities (notably certain enterprise features such as advanced access workflows/recording options) may require paid editions depending on your needs
- Operational complexity can be higher than simple SSH bastions due to certificate-based architecture and multi-component deployment
Teleport is well-suited for organizations that want consistent authentication and auditing across multiple infrastructure access methods. It provides a single access plane that scales from small teams to multi-cluster environments while improving credential hygiene and traceability.